corCTF 2024 - infiltration
- Author: jammy
- Date:
infiltration
Description: After successfully infiltrating the lemonthinker gang, we’ve obtained their current location - the UK. We’ve attained some security logs from a gang member’s PC, but need some help in answering information relating to these.
Solves: 164
Solution:
The challenge gives a file, security-logs.evtx, and a connection to a server. Let’s try connecting to the server:
1cordev@ubuntu:~$ nc be.ax 32222
2Hello agent. Thanks for your hard work in the field researching. We'll now ask you 6 questions on the information you've gathered.
3I'd like to take this opportunity to remind you that our targets are located in the United Kingdom, so their timezone is BST (UTC +1).
4We'd like to confirm what the username of the main user on the target's computer is. Can you provide this information?
We now know that we’ll be searching through the event logs to find the username of the main user on the computer.
The first step is to view the event logs. I’m going to use Event Viewer on windows in order to do this, but you can also use a tool like evtxdump to view the logs.
To use evtxdump, you can clone this repository, install the requirements python3 setup.py install and run the command python3 evtx_dump.py /home/cordev/infiltration/logs.evtx > logs.xml to convert the logs to xml.
From now on, I’ll be using Event Viewer to view the logs.
The first question asks what the username of the main user on the target’s computer is. We can find this by looking at a variety of sources - such as searching for logs with event ID 4647, which is a log off, or looking for when Credential Manager credentials are being read.
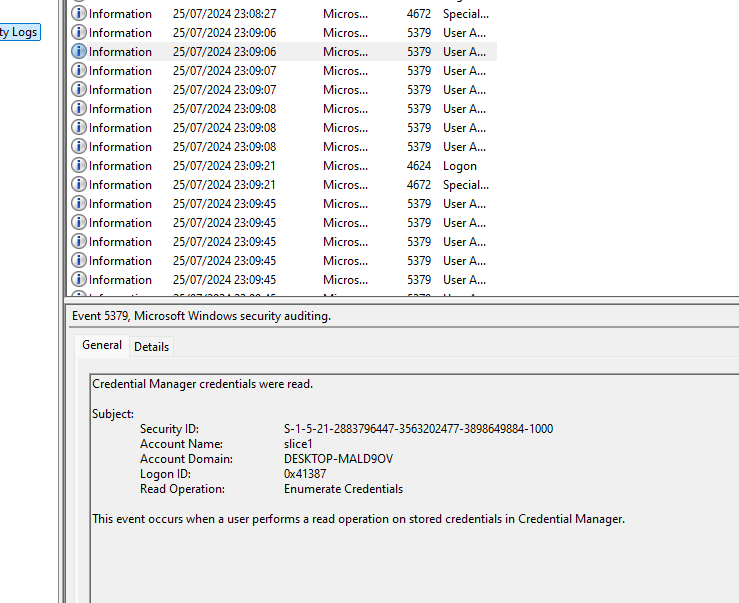
This gives us the username slice1.
The next question asks us what the target’s computer name is, after it was renamed.
An easy way to do this is to just look in the details for any events that are later in the file, like the below event:
This gives us the computer name lemon-squeezer.
A common mistake I saw being made was people putting in the account name LEMON-SQUEEZER$ instead of the computer name above. While these are similar, these are two different things, so they cannot be used interchangeably.
We are now given the 3rd question, which asks us for the maximum password age.
We can look for the event ID 4739, which shows us that some sort of domain policy was changed. While there are 5 events with this ID, we can simply take the final change.
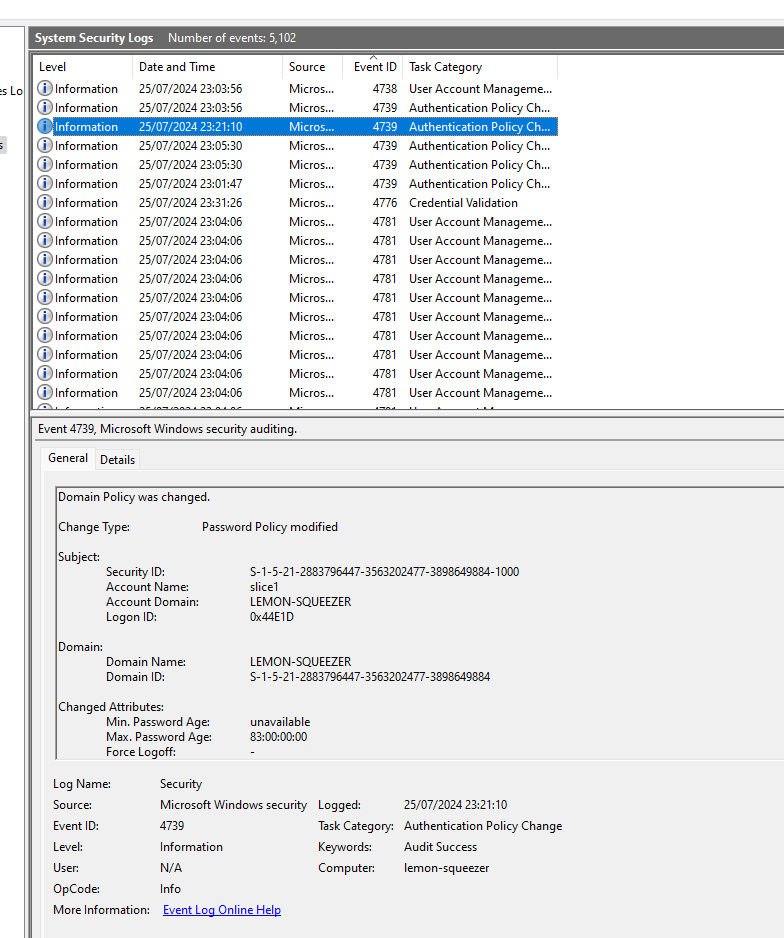
This shows us the maximum password age was set to 83 days.
We’re now asked for when the antivirus was turned off on the computer, as a UNIX timestamp.
While there are many indicators that the antivirus was turned off in this file, which happen over a variety of times, the one we’re most interested in is around 23:21:20 (in BST), where the Event ID 4699 indicated that many scheduled tasks for Windows Defender were deleted, such as Cleanup, Cache Maintenance, and Verfication.
The next bit of this challenge is where the most confusion came about. The question asks for a UNIX timestamp. However, depending on how you’re viewing the timestamp, the time you see will be in a different timezone. By default, Event Viewer logs times in UTC, but if you use Event Viewer to view logs, it will show these to you in your local timezone. This differs even more if you use evtxdump, which will show you the times in UTC. If not already, the time you get must be converted to UTC, then put into a timestamp.
This gives a timestamp of 1721946080 (However, a 10 second tolerance each way was allowed).
In retrospect, this part of the challenge caused a lot of confusion on the time conversion aspect - something I didn’t intend to happen. If I were to make this challenge again, I’d probably replace this question with one about what events are actually being audited.
The 5th question then tells us that a backdoor was installed on the computer, which created a new user, with us needing to provide the name of this user.
We can find this by looking for the event ID 4720, which shows us that a new user was created.
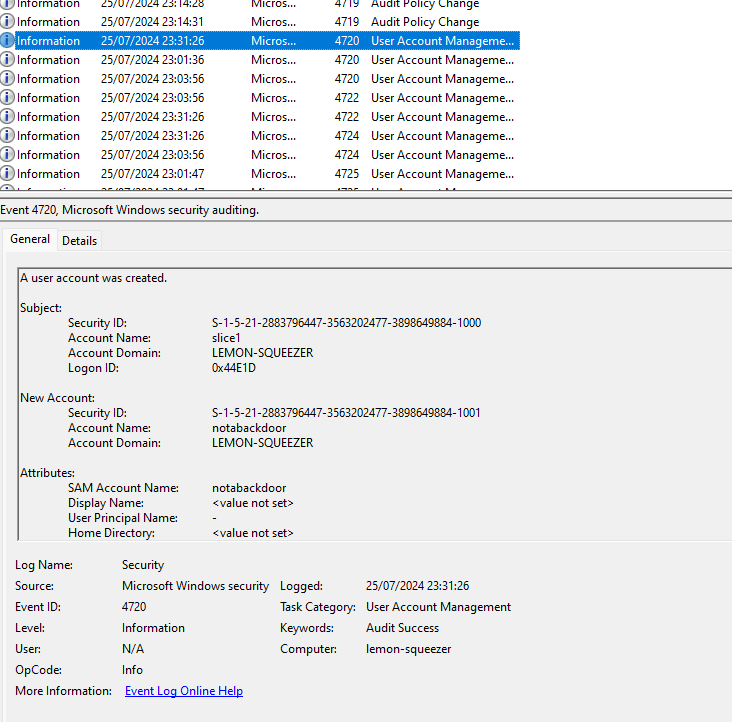
This gives us the very inconspicious username notabackdoor.
The final question asks us for the name of the group that the user created by the malware is part of, which has the greatest security risk. This question was reworded a few times during the CTF to be slightly clearer, as the original wording led to some slight confusion.
To solve this, you can go to the time the new user was created, 23:31:26 (BST) and look for event ID 4627. This lists the groups htat the user notabackdoor is part of.
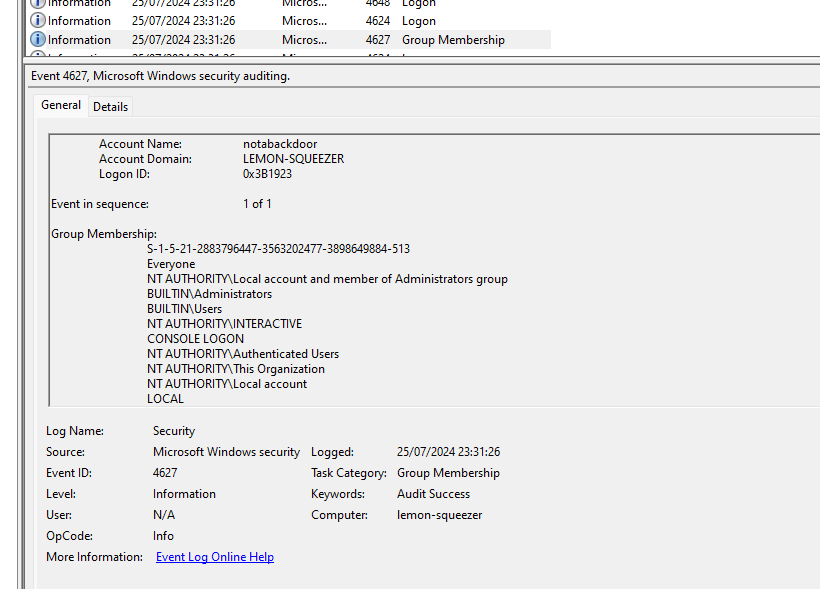
In this list, there are many groups, but the one with the greatest security risk is Administrators, which is the final answer.
After submitting all of these, you get the flag!
corctf{alw4y5_l3m0n_7h1nk_b3f0r3_y0u_c0mm1t_cr1m3}